Scenario 1: Modify client windows group policy settings
step1. Open the Group Policy Editor: press win+r, enter gpedit.msc and confirm
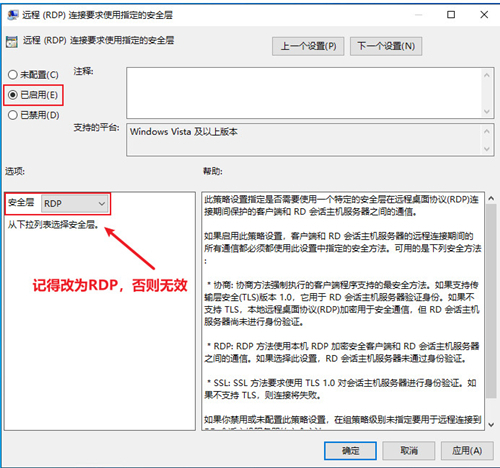
step2. Access path: Computer Configuration→Administrative Templates→Windows Components→Remote Desktop Services→Remote Desktop Session Host→Security
step3. Modify the settings, enable "remote (RDP) link requires the use of the specified security layer", select RDP as the security layer, and confirm
Solution 2: Modify the remote port
step1. Copy the following command to the local, and replace the text $new port with a reasonable port, it is recommended to be between 10000 and 30000.
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds\tcp" /v PortNumber /t reg_dword /d $new port
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v PortNumber /t reg_dword /d $new port
netsh advfirewall firewall add rule name=remote_port_tcp-$new port protocol=TCP dir=in localport=$new port action=allow
netsh advfirewall firewall add rule name=remote_port_udp-$new port protocol=UDP dir=in localport=$new port action=allow
net stop TermService && net start TermService
step2. Execute the above commands one by one, the last one will restart the remote service, and then the new port can be used for remote
Solution 3: Reset the winsock directory
step1. Open cmd on the local windows computer, execute netsh winsock reset, and it will take effect after restarting
Solution 4: Restart the server
step1. Restart the server