Principle: cc attack will simulate a large number of operations to access the site, squeezing out the resource space of normal visitors
Phenomenon: access to the site is significantly slow, the server cpu occupies a high number of tcp surge, up and down bandwidth run high
troubleshooting ideas.
Check the bandwidth graph. Normal access is more out than in. And cc attack, in and out of the traffic is basically the same.
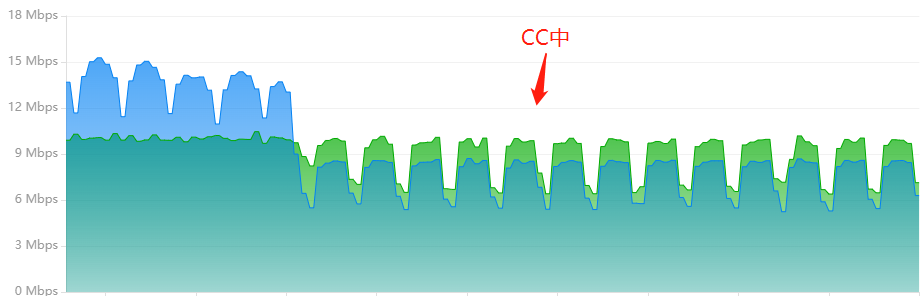
2. analyze the network link situation
1). Check the top 10 of tcp number on local ip
Command: netstat -an|grep ESTA|awk '{print $4}'|awk 'BEGIN {FS=":"} {print $1 "\n"}'|sort|uniq -c|head -11
2). View the live link traffic, the left side is the local receiving ip, the right side is the other ip
Command: yum install -y iftop && top
3. block specified ip test
Contact us to block the local ip with the highest number of links, and observe whether the resource usage decreases.
4. Processing
1). Use cdn
2). Determine the domain name is attacked, can be resolved to high security
2). Deactivate the attacked domain name and observe
3). Disable the attacked ip and observe